Master CompTIA Security+ SY0-701: Ultimate Cyber Defense 2024
Focused View
13:03:51
1. Welcome to Security Control Categories and Types.mp4
00:56
2. Security Controls Overview.mp4
09:14
3. Security Control Category Technical Controls.mp4
11:48
4. Security Control Category Managerial Controls.mp4
05:57
5. Security Control Category Operational Controls.mp4
03:55
6. Security Control Category Physical Controls.mp4
04:25
7. Validation.mp4
02:27
8. Part 2.mp4
10:11
1. Intro to summarize Security Concepts.mp4
00:21
2. CIA.mp4
23:34
3. Non-repudiation.mp4
03:48
4. AAA.mp4
08:33
5. Zero-Trust and Gap Analysis.mp4
11:11
6. Physical Security.mp4
04:42
7. Physical Security.mp4
10:20
8. Validation of Security Concepts.mp4
02:12
9. Validation of Security Concepts part 2.mp4
04:03
1. Intro to Change Management.mp4
00:37
2. Change Management Overview.mp4
07:29
3. Business Processes Impacting Security Operation.mp4
11:23
4. Technical Implications and Documentation.mp4
13:40
5. Practical Example for Change Control.mp4
10:54
6. Validation of Change Control with Security.mp4
02:10
7. Validation of Change Control with Security Part 2.mp4
03:16
1. Intro to Using Symmetrical Encryption.mp4
00:45
2. Symmetric Encryption Overview.mp4
11:02
3. Algorithm and Key Examples.mp4
06:14
4. Data at Rest Encryption Example.mp4
07:05
5. Data in Motion Encryption Examples with IPsec.mp4
14:16
6. Establishing a Shared Key.mp4
08:35
7. Reinforce and Validate.mp4
01:46
8. Reinforce and Validate Part 2.mp4
03:24
1. Intro to Asymmetrical Encryption.mp4
00:24
2. Asymmetrical Encryption Overview.mp4
15:34
3. Delivering Public Keys Using Digital Certificates.mp4
04:43
4. Using Digital Signatures.mp4
10:38
5. Using a Public Key to Encrypt.mp4
06:46
6. Using a Public Key to Encrypt.mp4
10:03
7. Validation.mp4
01:41
8. Validation Part 2.mp4
05:31
1. Intro to PKI and Certificates.mp4
00:35
2. PKI and Certs Overview.mp4
17:33
3. Self Signed Certs.mp4
04:47
4. Adding an Internal CA to as a Trusted CA.mp4
13:05
5. Using a CSR for Requesting a Certificate.mp4
12:31
6. Reinforce and Validate What We Have Learned.mp4
00:54
7. Reinforce and Validate What We Have Learned Part 2.mp4
03:44
1. Intro to Cryptography Tools and Methods.mp4
00:12
2. Cryptography Tools and Methods Overview.mp4
18:20
3. Security Modules.mp4
11:08
4. Obfuscation.mp4
09:18
5. Salting and Key Stretching.mp4
05:31
6. Open Public Ledger.mp4
11:10
7. Validation.mp4
01:05
8. Validation Part 2.mp4
04:16
1. Lets compare common themes in cybersecurity threats.mp4
01:20
2. Who are the attackers.mp4
07:20
3. What information do we use to classify threats.mp4
08:15
4. Where do we gain information on target systems.mp4
05:42
5. Where do we gain information on target systems Part 2.mp4
07:10
6. With all this information, what do we do with it.mp4
05:34
7. Challenge.mp4
01:49
8. Solution.mp4
05:09
1. Threat vectors.mp4
05:29
2. Threat indicators tell us more about threat vectors.mp4
12:35
3. Whos behind all this.mp4
09:41
4. ishing a subcategory.mp4
06:07
5. ishing a subcategory Part 2.mp4
04:55
6. Password Attacks.mp4
06:27
7. Challenge.mp4
01:24
8. Solution.mp4
02:36
1. The Attack Vector.mp4
02:29
2. Injection Attacks.mp4
12:53
3. Authentication Vulnerabilities.mp4
09:43
4. Session Attacks.mp4
09:30
5. Authentication Vulnerabilities.mp4
02:58
6. Authorization Vulnerabilities.mp4
05:21
7. Cross-Site Scripting - XSS.mp4
01:45
8. Memory Management.mp4
04:38
9. Challenge.mp4
01:26
10. Solution.mp4
02:17
1. Indicators of Malicious Activity.mp4
00:48
2. Social Engineering Indicators.mp4
03:05
3. Network Indicators.mp4
08:34
4. System Indications.mp4
05:55
5. Access Indicators.mp4
07:25
6. Pathways for malicious activity.mp4
07:02
7. Challenge.mp4
01:42
8. Solution.mp4
08:03
1. Identifying those indicators.mp4
01:43
2. Social Engineering Remedies.mp4
08:34
3. Network Remedies.mp4
10:28
4. System Remedies.mp4
10:20
5. Access Remedies.mp4
08:49
6. Challenge.mp4
00:39
7. Solution.mp4
04:11
1. Software Development Life Cycle - SDLC.mp4
10:42
2. Software Development Life Cycle - SDLC Part 2.mp4
01:56
3. Software Testing.mp4
12:00
4. Security Testing.mp4
07:23
5. Application Security Controls.mp4
06:36
6. Challenge.mp4
00:27
7. Solution.mp4
05:57
1. Introducing IDS and IPS.mp4
01:53
2. Lets start by understanding what IDS and IPS is..mp4
02:39
3. Understanding Rules.mp4
06:16
4. IDS and IPS Placement.mp4
09:15
5. Bringing all of them together.mp4
01:41
6. What is a SOAR.mp4
03:53
7. What is a SIEM.mp4
04:40
8. Challenge.mp4
04:20
9. Solution.mp4
06:11
1. Introduction.mp4
00:40
2. Overview.mp4
04:39
3. Cloud Architectures.mp4
19:19
4. Application Architectures.mp4
09:08
5. Network Architectures.mp4
22:20
6. Segmentation Example.mp4
09:44
7. Validation.mp4
02:16
8. Solution.mp4
08:23
More details
Course Overview
This comprehensive Security+ certification course prepares you for the SY0-701 exam while equipping you with essential cybersecurity skills to protect organizations from modern threats.
What You'll Learn
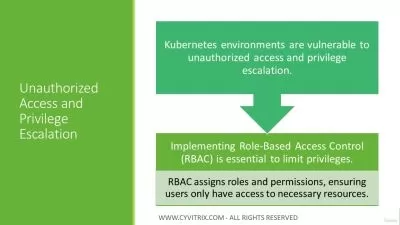
- Implement security controls across technical, operational and physical domains
- Master encryption methods including symmetric, asymmetric and PKI systems
- Identify threats, vulnerabilities and implement effective mitigation strategies
Who This Is For
- Aspiring cybersecurity professionals seeking Security+ certification
- IT administrators transitioning to security roles
- Network engineers expanding their security knowledge
Key Benefits
- Hands-on practice with encryption tools and security implementations
- Real-world threat analysis and defense techniques
- Preparation for one of IT's most valuable security certifications
Curriculum Highlights
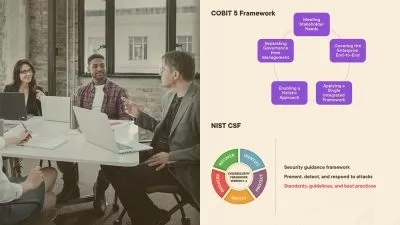
- Security Controls & CIA Fundamentals
- Cryptography & PKI Mastery
- Threat Analysis & Mitigation Strategies
Focused display
Category
- language english
- Training sessions 120
- duration 13:03:51
- Release Date 2025/05/21