Master CSSLP: Ultimate Secure Software Development Guide
Focused View
7:28:54
1 -Introduction.mp4
13:20
2 -About Exam.mp4
02:15
1 - Domain -1 Content.html
1 -0-Introduction.mp4
02:34
2 -1-CIA Guideline.mp4
07:23
3 -3-Authentication.mp4
10:36
4 -4-Authorization.mp4
02:29
5 -5-Accountability.mp4
04:18
6 -6-Non Repudiation.mp4
01:34
7 -7-Secure Development Lifecycle (SDL).mp4
03:20
8 -8-SDL Components.mp4
02:29
9 -Summary and Recap.mp4
01:04
1 -0-Introduction.mp4
01:09
2 -1-System Tenets.mp4
03:17
3 -2-Secure Design Tenets.mp4
06:01
4 -4-Adversaries.mp4
05:12
5 -Summary and Recap.mp4
01:28
6 -3-Security Models.mp4
07:19
1 - Domain 2 - Content.html
1 -0.Introduction.mp4
01:14
2 -1. Functional Requirements.mp4
05:20
4 -3. Summary and Recap.mp4
02:27
1 -0. Introduction.mp4
01:37
2 -1. Regulations and Compliance.mp4
05:02
3 -2. Data Classification.mp4
06:16
4 -3. Privacy.mp4
06:57
1 -0.Introduction.mp4
02:01
2 -2. MisuseAbuse Cases.mp4
05:07
3 -3. Requirements Traceability Matrix.mp4
04:32
4 -4. Software Acquisition.mp4
07:17
5 -5. Summary.mp4
00:57
1 - Secure Software Architecture and Design.html
1 -Introduction.mp4
00:40
2 -Perform Threat Modeling.mp4
21:51
3 -Defining the Security Architecture.mp4
05:33
4 -Summary and Recap.mp4
00:29
1 -Performing Architectural Risk Assessment.mp4
01:52
2 -Model (Nonfunctional) Security Properties and Constraints.mp4
01:49
3 -Model and Classify Data.mp4
03:03
4 -Perform Security Architecture and Design Review.mp4
01:55
4 - Evaluate and Select Reusable Secure Design.html
5 -Define Secure Operational Architecture.mp4
02:49
6 -Introduction.mp4
01:21
7 -Use Secure Architecture and Design Principles, Patterns, and Tools.mp4
02:40
8 -Performing Secure Interface Design.mp4
02:58
9 -9-Summary.mp4
00:58
1 - Content.html
1 -0 Intro.mp4
01:14
2 -1-Declarative vs. Imperative Security.mp4
03:43
3 -2-Memory Management.mp4
04:09
4 -3-Error Handling.mp4
02:29
5 -4-Interface Coding.mp4
03:32
6 -5-Primary Mitigation.mp4
04:03
7 -6-Learning from Past Mistakes.mp4
02:57
8 -7-Secure design principles.mp4
03:35
9 -8-Interconnectivity.mp4
04:20
10 -9-Cyrptographics Failures.mp4
04:56
11 -11-General Programings Failures.mp4
04:59
11 - 10-Input Validation Failuers.html
12 -12-Technology Solution.mp4
04:37
13 -Summary and Recap.mp4
00:56
1 -0-Introduction.mp4
01:18
2 -1-Code Analysis.mp4
08:01
3 -2-CodePeer Review.mp4
03:57
4 -3-Code Review Objectives.mp4
03:46
5 -4-Additional Sources of Vulnerability Information.mp4
02:02
6 -5-Top25.mp4
03:27
7 -6-OWASP Vulnerability.mp4
01:02
8 -7-Common Vulnerabilities.mp4
05:07
9 -8-Summary.mp4
00:46
1 -0-Introduction.mp4
01:25
2 -1-Security Risks.mp4
03:58
3 -2-Implement Security Controls.mp4
04:13
4 -4-Anti-tampering Techniques.mp4
04:59
4 - 3-Applying Security.html
5 -6-Primary Mitigations.mp4
03:58
5 - 5-Defensive Coding Techniques.html
6 -7-Secure Integration of Components.mp4
04:33
7 -8- Summary and Recap.mp4
01:47
8 - Content.html
1 -Introduction.mp4
01:18
1 - Content.html
2 -2-Security Test Cases.mp4
04:28
3 -3-Attack Surface Evaluation.mp4
04:19
4 -4-Penetration Testing.mp4
05:04
5 -5-Common Methods.mp4
08:44
6 -6-Summary and Recap.mp4
01:23
1 -0-Introduction.mp4
01:22
2 -2-Develop a Security Testing Strategy and A Plan.mp4
04:27
3 -3-Functional Security Testing.mp4
03:11
4 -4-Non Functional Security Testing - p.mp4
03:11
5 -5-Testing Techniques.mp4
03:59
6 -6-Environment.mp4
03:47
7 -7-Standards.mp4
04:31
8 -8-Crowd Sourcing.mp4
02:16
9 -9-Summary and Recap.mp4
01:27
1 -0 - Introduction.mp4
02:42
1 - Content.html
2 -1 - Secure Configuration and Version Control.mp4
03:51
3 -2 - Define Strategy and Roadmap.mp4
04:40
4 -3 - Manage Security Within a Software Development Met.mp4
04:03
5 -4 Identify Security Standards and Frameworks.mp4
04:52
6 -5 - Define and Develop Security Documentation.mp4
03:20
7 -6 - Develop Security Metrics.mp4
03:58
8 -7 - Decommission Software.mp4
04:19
9 -8 Report Security Status.mp4
03:00
10 -9 Summary and recap.mp4
02:17
1 -0-Introduction.mp4
00:57
2 -1 - Incorporate Integrated Risk Management.mp4
05:39
3 -2 - Implement Continuous Improvement.mp4
03:12
4 -3 Summary and Recap.mp4
02:40
1 - Content.html
1 -0 - Introduction.mp4
01:33
2 -2-Perform Operational Risk Analysis.mp4
04:51
3 -3-Release Software Securely.mp4
04:18
4 -4-Securely Store and Manage Secur.mp4
03:55
5 -5-Ensure Secure Installation.mp4
05:01
6 -6-Perform Post-Deployment Securit.mp4
03:00
7 -7-Summary.mp4
02:14
1 -Introduction.mp4
01:51
2 -OSATO.mp4
02:27
3 -Perform Information Security Continuous Monitoring.mp4
04:12
4 -Support Incident Response.mp4
03:55
5 -Perform Patch Management.mp4
02:31
6 -Perform Vulnerability Management.mp4
03:01
7 -Runtime Protection.mp4
03:10
8 -Support Continuity of Operations.mp4
04:42
9 -Integrate Service Level Objectives and Service Level Agreements.mp4
04:32
10 - Summary.html
1 - Content.html
1 -1-Implement Software Supply Chain Risk Management.mp4
02:51
1 - 0-Introduction.html
2 -2-Analyze Security of Third-Party Software.mp4
04:09
3 -3-Verify Pedigree and Provenance.mp4
03:04
4 - 4-Summary and Recap.html
1 -1-Ensure Supplier Security Requirements in the Acquisition Process.mp4
03:28
1 - 0-Introductoin.html
2 -2-Support Contractual Requirements.mp4
04:50
3 - 3-Summary.html
More details
Course Overview
This comprehensive CSSLP certification course equips you with essential secure software development skills, covering the entire lifecycle from design to deployment. Master industry best practices through hands-on learning, practice tests, and expert-curated resources.
What You'll Learn
- Core security concepts including CIA, authentication, and non-repudiation
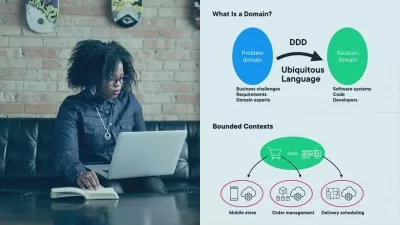
- Secure software architecture design and threat modeling
- Secure coding practices and vulnerability mitigation techniques
Who This Is For
- Software Security professionals and architects
- Application Security Specialists
- Software Project/Program Managers
Key Benefits
- CSSLP exam readiness with practice questions and tests
- Comprehensive coverage of all 8 security domains
- Practical skills for implementing secure SDLC
Curriculum Highlights
- Secure Software Core Concepts
- Secure Requirements & Architecture
- Secure Implementation & Testing
Focused display
Category
- language english
- Training sessions 121
- duration 7:28:54
- Release Date 2025/06/02