Master Ethical Hacking with Python: 2024 Pro Guide
Focused View
5:06:01
01-Description-of-Training.html
02-Video-Overview-(12-48-).mp4
12:48
01-Introduction-(12-48-).mp4
12:48
01-Install-Linux-(13-55-).mp4
13:55
02-Setup-your-lab-(9-47-).mp4
09:47
03-Adjust-Kali-Display-(7-33-).mp4
07:33
04-Install-Windows-VM-(10-25-).mp4
10:25
01-Kali-Linux-File-System-(5-54-).mp4
05:54
02-Kali-Linux-OS-(5-21-).mp4
05:21
03-Kali-Linux-Terminal---S-(5-43-).mp4
05:43
04-Terminal-Help-(3-05-).mp4
03:05
05-Update---Upgrade-(2-11-).mp4
02:11
01-Python2-vs-Python3-(2-11-).mp4
02:11
02-Python-(7-30-).mp4
07:30
03-IDE-(10-01-).mp4
10:01
04-Working-with-IDE-(5-32-).mp4
05:32
05-First-Script-(4-02-).mp4
04:02
06-Working-with-Strings-(3-31-).mp4
03:31
07-Modules-and-Functions-(14-22-).mp4
14:22
08-Varaibles-(14-14-).mp4
14:14
09-Working-with-Functions-(7-38-).mp4
07:38
10-User-Input-(8-04-).mp4
08:04
11-Program-to-scan-a-system-(17-43-).mp4
17:43
12-If-Statement-(11-17-).mp4
11:17
13-For-Loop-(7-30-).mp4
07:30
14-Documentation-(1-25-).mp4
01:25
01-Prebuild-Python-Packages-(3-04-).mp4
03:04
02-EH-using-Python-(3-07-).mp4
03:07
03-Install-Packages-(4-16-).mp4
04:16
04-Network-Discovery-Script-(6-45-).mp4
06:45
05-Network-Discovery---Part-2-(5-55-).mp4
05:55
06-MITM-Attack-(11-10-).mp4
11:10
07-MITM-Attack-Part-2-(15-18-).mp4
15:18
08-MITM-Attack-Part-3-(5-00-).mp4
05:00
09-MITM-Attack-Part-4-(7-53-).mp4
07:53
10-MITM-Attack-Part-5-(6-43-).mp4
06:43
11-Packet-Sniffer-(7-08-).mp4
07:08
12-Filters-(4-14-).mp4
04:14
13-HTTP-Traffic-(8-37-).mp4
08:37
14-Password-Sniffer-(2-55-).mp4
02:55
15-Port-Forwarding-(9-26-).mp4
09:26
Hacking using Python From A to Z audio.zip
More details
Course Overview
This comprehensive course teaches you how to leverage Python for ethical hacking, from basic scripting to advanced network attacks. Gain hands-on experience with Kali Linux and build real-world security tools.
What You'll Learn
- Python programming fundamentals for security applications
- Network discovery and MITM attack techniques
- Packet sniffing, password extraction, and port forwarding
Who This Is For
- Aspiring ethical hackers wanting Python skills
- Security professionals expanding their toolset
- Programmers interested in cybersecurity
Key Benefits
- Hands-on labs with Kali Linux environment
- Build functional security tools from scratch
- Learn offensive security techniques ethically
Curriculum Highlights
- Kali Linux setup and Python environment
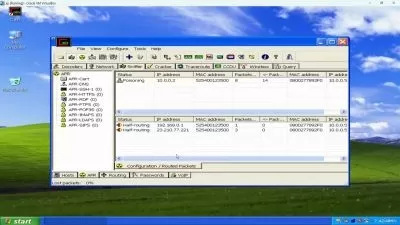
- Network scanning and discovery scripts
- Advanced MITM attacks and traffic analysis
Focused display
Category
- language english
- Training sessions 40
- duration 5:06:01
- Release Date 2025/04/19