Master Linux Security: Ultimate 2024 Protection Guide
Focused View
11:30:59
1.1 Introduction to Linux Users.mp4
03:09
1.2 Principle of Least Privilege.mp4
04:58
1.3 Accessing the Repository and Network Map.mp4
03:54
1.4 The id Command.mp4
07:03
2.1 Secure Passwords.mp4
03:30
2.2 Setting the Password.mp4
06:13
2.3 Generating Passwords with openssl and KeePass.mp4
12:23
2.4 The passwd and shadow Files.mp4
08:11
2.5 Password Settings.mp4
10:02
2.6 Password Policy Configuration.mp4
11:54
3.1 Logging in as a Typical User by Password.mp4
14:23
3.2 Logging in as an Enterprise User.mp4
14:29
3.3 Locking the System.mp4
04:35
3.4 SSH Basics.mp4
09:23
3.5 SSH and Linux in the Cloud.mp4
17:17
4.1 The su command.mp4
06:37
4.2 Using the sudo command.mp4
08:57
4.3 sudoers.mp4
07:03
4.4 Assigning a Regular User sudo Permissions.mp4
07:11
5.1 Introduction to Linux OS Security.mp4
02:36
5.2 Defense in Depth.mp4
03:27
5.3 The CIA Triad.mp4
03:07
6.1 Updating Debian and Ubuntu.mp4
12:08
6.2 More apt and Repositories.mp4
10:25
6.3 Updating Fedora, Red Hat, and CentOS.mp4
03:39
6.4 Installing Security Updates Only.mp4
10:44
6.5 Updating SUSE.mp4
03:13
6.6 Updating Arch.mp4
03:20
7.1 systemctl Basics.mp4
03:00
7.2 Reducing the Attack Surface.mp4
14:06
7.3 Creating a Degraded System.mp4
05:09
7.4 Repairing a Degraded System.mp4
08:35
7.5 systemd states.mp4
05:57
8.1 10 Steps to a Secure Linux Server (Part I).mp4
06:40
8.2 10 Steps to a Secure Linux Server Server (Part II).mp4
04:42
8.3 Wired & Wireless Security in Linux.mp4
13:00
8.4 Securing GRUB.mp4
13:24
9.1 AppArmor Basics.mp4
08:02
9.2 AppArmor Profiles.mp4
15:15
9.3 AppArmor and Apache Example.mp4
10:48
9.4 SELinux Basics.mp4
12:17
10.1 What is a Firewall.mp4
02:55
10.2 Types of Linux-based Firewalls.mp4
02:10
10.3 Zero-Trust Environment Mindset.mp4
03:03
11.1 UFW Introduction.mp4
02:02
11.2 Setting up UFW.mp4
06:11
11.3 Configuring UFW.mp4
10:21
12.1 firewalld Introduction.mp4
02:22
12.2 Installing and enabling firewalld.mp4
06:50
12.3 Configuring and Testing firewalld.mp4
14:56
12.4 Lock it Down!.mp4
02:32
12.5 Returning the System to its Original State.mp4
02:06
13.1 Introduction to nftables and the nft command.mp4
02:34
13.2 nftables Setup.mp4
04:05
13.3 Tables Chains Rules.mp4
02:31
13.4 Building the nftables Configuration (Part I).mp4
08:41
13.5 Building the nftables Configuration (Part II).mp4
08:39
13.6 Saving and Restoring the nftables Configurations.mp4
08:36
13.7 Translating iptables to nftables.mp4
07:49
14.1 Review of SSH.mp4
01:47
14.2 Using Keys to connect via SSH.mp4
12:57
14.3 The sshd config file.mp4
03:19
14.4 Modifying the default SSH port.mp4
07:32
14.5 Disabling Password-based SSH.mp4
02:57
14.6 Disabling root login via SSH.mp4
02:33
14.7 Exclusive SSH Groups.mp4
04:37
14.8 Authentication Settings.mp4
10:06
14.9 Terminating SSH Connections (Part I).mp4
07:45
14.10 Terminating SSH Connections (Part II).mp4
06:53
15.1 RAID 1.mp4
05:32
15.2 RAID 5.mp4
05:16
15.3 RAID 10 and ZFS.mp4
11:36
15.4 Backup!.mp4
10:12
16.1 chmod.mp4
12:09
16.2 chown and chgrp.mp4
14:46
16.3 Encryption in Linux.mp4
08:34
16.4 Linux Encoding and Hashing.mp4
13:18
17.1 Viewing Processes.mp4
09:49
17.2 Ending Processes with Commands.mp4
05:36
17.3 Ending Processes with top.mp4
06:44
18.1 Logging in Linux - The Journal.mp4
10:52
18.2 Logging in Linux - rsyslog Part I.mp4
10:08
18.3 Logging in Linux - rsyslog Part II.mp4
08:22
18.4 Auditing in Linux.mp4
10:21
18.5 Nmap.mp4
08:57
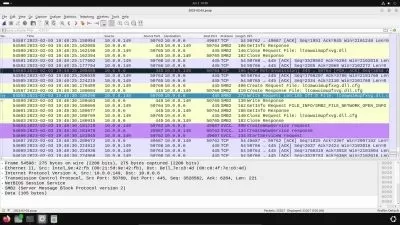
18.6 Wireshark.mp4
12:55
18.7 Additional Tools.mp4
03:06
Learning objectives.mp4
00:58
Learning objectives (1).mp4
00:58
Learning objectives (2).mp4
00:41
Learning objectives (3).mp4
00:54
Learning objectives (4).mp4
01:09
Learning objectives (5).mp4
00:25
Learning objectives (6).mp4
01:59
Learning objectives (7).mp4
01:34
Learning objectives (8).mp4
00:41
Learning objectives (9).mp4
00:38
Learning objectives (10).mp4
00:46
Learning objectives (11).mp4
00:22
Learning objectives (12).mp4
00:50
Learning objectives (13).mp4
01:34
Learning objectives (14).mp4
01:18
Learning objectives (15).mp4
01:30
Learning objectives (16).mp4
00:34
Learning objectives (17).mp4
00:25
Learning objectives (18).mp4
00:57
Linux Security - Basics and Beyond Introduction.mp4
03:03
Linux Security - Basics and Beyond Summary.mp4
01:23
Module Introduction.mp4
00:46
Module Introduction (1).mp4
01:37
Module Introduction (2).mp4
02:21
Module Introduction (3).mp4
01:48
More details
Course Overview
This comprehensive course takes you from Linux security basics to advanced protection techniques, equipping you with essential skills to secure systems effectively.
What You'll Learn
- Fundamentals of Linux system security
- Advanced threat protection techniques
- Best practices for secure system administration
Who This Is For
- System administrators looking to enhance security
- IT professionals transitioning to Linux environments
- Developers needing secure deployment skills
Key Benefits
- 11.5 hours of hands-on security training
- Real-world applicable security strategies
- Lifetime access to course materials
Curriculum Highlights
- Linux Security Fundamentals
- User Access and Permission Management
- Network Security and Hardening
Focused display
Category
- language english
- Training sessions 112
- duration 11:30:59
- Release Date 2025/05/27