Ultimate Cyber Security Mastery: Zero to Pro 2024
Focused View
4:29:03
1 -Welcome to the course.mp4
02:30
2 -Course Objectives.mp4
03:34
3 -How To Clone VM.pdf
3 -Setting up the Cyber Home Lab Network.mp4
08:01
1 -Understanding Cybersecurity.mp4
11:36
2 -Different Cyber Teams.mp4
02:18
1 -Recognizing Vulnerabilities.mp4
06:04
2 -Types of Cyber Attacks.mp4
16:51
1 -Fundamentals of Network Security.mp4
10:34
2 -Vulnerability Management.mp4
09:30
3 -Endpoint Security and Secure Configurations.mp4
08:35
4 -Incident Response and Recovery.mp4
06:46
1 -Understanding Cybersecurity Laws and Regulations.mp4
01:28
2 -Ethical Hacking and Penetration Testing.mp4
11:09
3 -Ethics in Cybersecurity.mp4
06:56
1 -Understanding Data Privacy Concepts and Principles.mp4
05:45
2 -Strategies for Data Minimization and Anonymization.mp4
03:28
3 -Implementing Data Protection Controls.mp4
01:38
1 -Overview of the Software Development Lifecycle (SDLC).mp4
05:29
2 -Secure Coding Practices and Principles.mp4
00:50
3 -Reverse Engineering.mp4
01:42
4 -Security Testing.mp4
04:23
1 -Reconnaissance using OSINT.mp4
03:39
2 -Network Scanning using Nmap.mp4
08:14
3 -DDOSDOS using Hping3.mp4
05:50
4 -DOS Attack Using Metasploit.mp4
06:37
5 -MITM (Man In the Middle) using Ettercap (ARP Poisoning).mp4
05:18
6 -Wireless Password Hacking.mp4
07:03
7 -Using Google Hacking Database (GHDB).mp4
06:28
8 -Using Metasploit to Hack Windows System through Phishing.mp4
14:11
9 -Brute Force Attacks using Hydra (RDP).mp4
12:56
10 -How to Create a Botnet using BeEF.mp4
10:20
11 -Vulnerability Assessment using OpenVAS.mp4
07:07
1 -Building Cyber Awareness at the Work Place, Schools and at Home.mp4
15:33
1 -Introduction to Cloud Security.mp4
06:53
2 -Securing Cloud Infrastructure and Data.mp4
05:05
3 -Securing Cloud-Native Applications.mp4
03:41
1 -IoTOT Technologies and Infrastructure.mp4
17:10
1 -SPECIAL LESSON Career Pathways in Cybersecurity.mp4
03:51
1 -Sample-Penetration-Test-Report-PurpleSec.pdf
More details
Course Overview
This comprehensive cybersecurity course transforms beginners into skilled professionals through hands-on training in threat detection, network defense, and ethical hacking techniques using Kali Linux and industry-standard tools.
What You'll Learn
- Fundamentals of confidentiality, integrity, and availability in cybersecurity
- Network scanning with Nmap and vulnerability assessment using OpenVAS
- Ethical hacking techniques including MITM attacks and penetration testing
Who This Is For
- IT professionals transitioning to cybersecurity roles
- Business leaders managing organizational digital security
- Tech enthusiasts seeking hands-on hacking defense skills
Key Benefits
- No prior experience required - starts from foundational concepts
- 200+ slides and practical demos with Kali Linux
- Covers compliance, cloud security, and career pathways
Curriculum Highlights
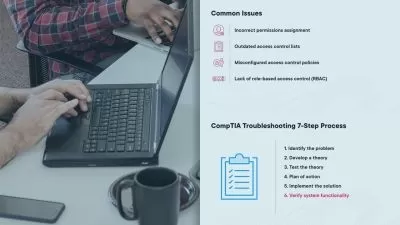
- Cyber threats recognition & vulnerability management
- DDoS/MITM attacks and penetration testing demos
- Cloud/IoT security and capstone project
Focused display
Category
- language english
- Training sessions 38
- duration 4:29:03
- Release Date 2025/05/18